Profile¶
To participate in the Taskhive network, a profile is needed for representation. A profile can be as detailed and public, or bare-bones and private, as desired. The bare minimum profile will consist of only a public key. A full profile might include work samples, an avatar image, and lengthy reputation feedback.
Identity¶
In Taskhive, profiles are identified by a cryptographic public key. This public key is necessary to verify authenticity of correspondence, sign contracts, and build a reputation on the network. The client application can generate this key, or an existing compatible key can be imported.
Profile public keys are ECDSA Secp256k1 keys (identical to keys used in bitcoin). This means that any key generated for a bitcoin wallet will also work for identity inside of taskhive.
Compatible Keys¶
For convenience and compatibility with other reputation networks, GPG keys may optionally be added to a profile. For established GPG users, this can serve to import existing Web-of-Trust reputation to the network.
Default Identicons¶
Default profile identicons are generated by feeding the compressed public key to the Identicon library. Due to the higher probability of collision and confusion, it is recommended to upgrade to a Qrcode-art avatar.
Example default pixel-art avatars generated from public key.
Qrcode-art Avatars¶
Qrcode-art avatars are generated by feeding a low resolution image to the CuteR library, along with the encoded profile’s compressed public key data. The binary data is then embedded into profiles as a base64 string for display on the client.

Example Qrcode avatars generated via the CuteR library.
Feedback¶
Positive, neutral and negative feedback can be left for profiles on taskhive. Feedback is categorized into three basic types:
- Unsolicited – this type of feedback carries the least weight and may contain spam, libel or unrelated personal drama. Nevertheless, unsolicited feedback is necessary on a p2p network to promote transparency and to combat corruption. An example legitimate use of unsolicited feedback is when a profile is misrepresenting skills by stealing samples of other freelancers. Unsolicited feedback carries a neutral score (0).
- Solicited-Transaction – this type of feedback is directly tied to a transaction and carries the most weight. Any parties to a transaction may leave this type of feedback, including escrow agents. Solicited-transaction feedback can carry a negative (-1), neutral (0), or positive (+1) score rating.
- Rebuttal – this type of feedback is used against both unsolicited and solicited-transaction feedback to present a rebuttal against false or inappropriate claims, provide public evidence to protect reputation, or to notify the public of malicious feedback abuse. Rebuttal feedback carries a neutral score (0).
Feedback data for all profiles is continuously circulating throughout the network, bouncing between peers so that it is always available upon request. Each client is opted-in automatically to participating in this crucial broadcast service, but may opt-out manually. For mobile users, it is only enabled when connected over Wi-fi.
Reputation Tally¶
Profiles display a reputation tally based on signed feedback data. Tallies are displayed as a hexagonal grid, color coded to represent negative and positive encounters.
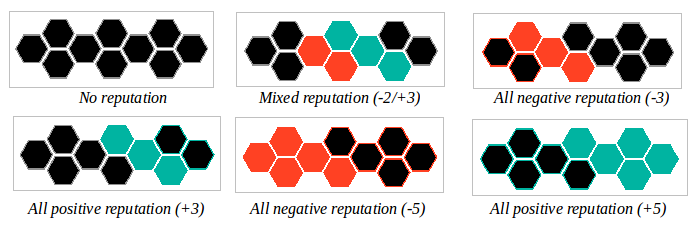
The feedback data used in tallying the reputation score comes from feedback broadcast across the network, but not all data is equal. It must be filtered against local criteria:
- Local Follow List – this list includes profiles manually followed, or profiles opted-to-follow when leaving positive Solicited-Transaction feedback. Feedback scores given by these profiles will be included.
- Local Ignore List – this list includes profiles manually ignored, or profiles opted-to-ignore when leaving negative Solicited-Transaction feedback. Feedback scores givenby these profiles will be ignored.
Skills¶
For freelancers, the skills section of a profile lists what categories the profile is offering services in. An example of the skills that might be listed in a profile are:
| Writing Development | Editing Data entry | Design Video editing | Voice acting Research |
Work Samples¶
Work samples may be provided as unsafe links to third-party websites. Accessing these links directly may lead to reduced privacy or complete deanonymization. Using Tor or a trusted VPN is recommended.
Third-party Profile Authentication¶
Authentication of third-party profiles and portfolios is possible through a signed string containing the hash of the profile or portfolio’s address, combined with the taskhive profile’s public key. This string can then be posted anywhere on or inside the third-party profile, or as instructed inside taskhive.
When adding work samples, taskhive will automatically detect the relative account to the work sample and provide instructions for authenticating it.
Proving ownership of an account does not guarantee ownership of work samples, as accounts can be cloned or spoofed with stolen work. It is recommended to use due diligence and search on a major search engine for work samples, either through titles and body content or reverse image searching.
Privacy Preferences¶
Depending on the work involved, it may be more practical for some workers to use email or another form of instant messaging (IRC, XMPP, etc) to discuss a task on a regular basis. A profile’s privacy preferences let potential clients know what form of contact is acceptable to avoid future misunderstandings.